PARTNER CONTENT FROM VERIZON MEDIA
The rapid expansion of connected home and personal devices using the Internet means cybercriminals’ opportunities have increased.
As video streaming soars, criminals are following the money and they are stepping up their game.
Pay TV broadcasters, sports franchises, Hollywood studios are looking to cash in on the seismic demand for viewing OTT on demand, but as M&E increasingly moves distribution online the frequency, severity and sophistication of cyberattacks puts streaming services under constant threat.
Indeed, cybersecurity has become a high-tech game where thieves innovate their attacks faster than most organizations can adapt their defenses.
Does that mean it could happen to you? Alarmingly, a Verizon Media survey of streaming media service executives shows it probably already has.
Download the Full Verizon Media Report Here
Half of the survey participants said security breaches had degraded their service’s user experience. A third had suffered a service outage, and 13% had content misappropriated.
Few respondents felt completely prepared for an attack of any description. Most consider themselves moderately prepared. Given the rapid evolution of cyberattack approaches is that good enough?
Vulnerabilities
The problem with streaming is that there are so many points of vulnerability for a criminal to exploit. In security parlance the ‘surface area’ is huge and expanding. Every point at which users access media is a potential weak spot.
For example, customer payment details, email addresses, physical addresses, names and passwords are a treasure trove difficult for hackers to resist. A large variety of supported client devices — laptops, connected TVs, mobile phones, consoles — provide a multiplicity of Achilles’ heels.

In 2020, the number of so-called API attacks grew rapidly. One cybersecurity software company saw a 40% increase in malicious API traffic during the third week of April 2020. Attackers were targeting a single weakness — a login API for an Android application.
Other types of attack include Distributed denial-of-service (DDoS) which use artificial traffic to disrupt a site or service, making it inaccessible or slow to respond to legitimate users. Hackers may launch a DDoS simply to cause mischief or create a diversion for another attack or even aid a competitive service. The number of such attacks sized at least 100 Gbps grew an alarming 275% in the first half of 2020.
A favorite of hackers is Phishing, a type of attack which aims to trick users into unwittingly installing malware or revealing personal information such as credit card information.
Verizon Media reports hackers stole 100 terabytes of data, including four unreleased Hollywood movies, by mining LinkedIn for information on an (unnamed) studio’s employees. Using this data, they selected employees and, posing as a work colleague, sent them emails containing malware.
Take Security to the Cloud
The report doesn’t just outline the problems. It has some security prescriptions too. These are already in play but Verizon Media contends that they need to be Fort Knoxed by moving defense into the cloud.
This makes sense given the increasing size, sophistication and duration of DDoS attacks. Shifting more of the solution into the cloud and CDNs provides the scale and simplicity needed to keep pace with changing DDoS attack strategies.
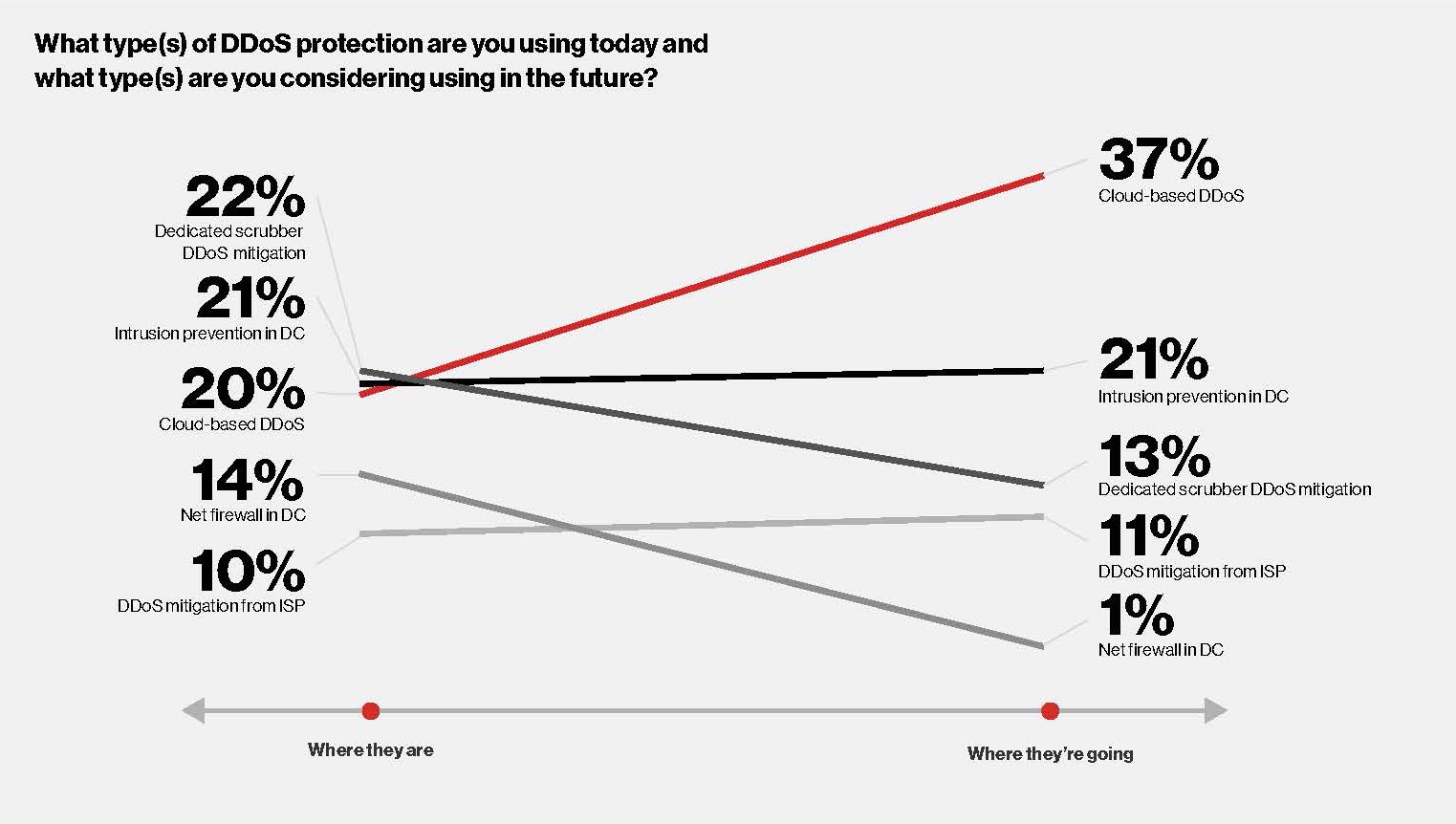
DDoS protection is often built into cloud provision from AWS, Microsoft Azure, or GCP for tasks such as compute, database and storage functions. However, specialized support usually requires a separate contract.
Another option is for streaming services to look to CDN providers for DDoS protection. Like cloud providers, CDNs can scale to handle the largest attacks and leverage their architecture to distribute protection throughout the delivery cloud.
Firewalls
Another option is to get a Web application firewall (WAF). WAFs are deemed essential in eliminating application vulnerabilities that hackers exploit in DDoS, app, credential stuffing and phishing attacks. They protect servers by analyzing HTTP/HTTPS traffic and applying rules to conversations between the server and clients.
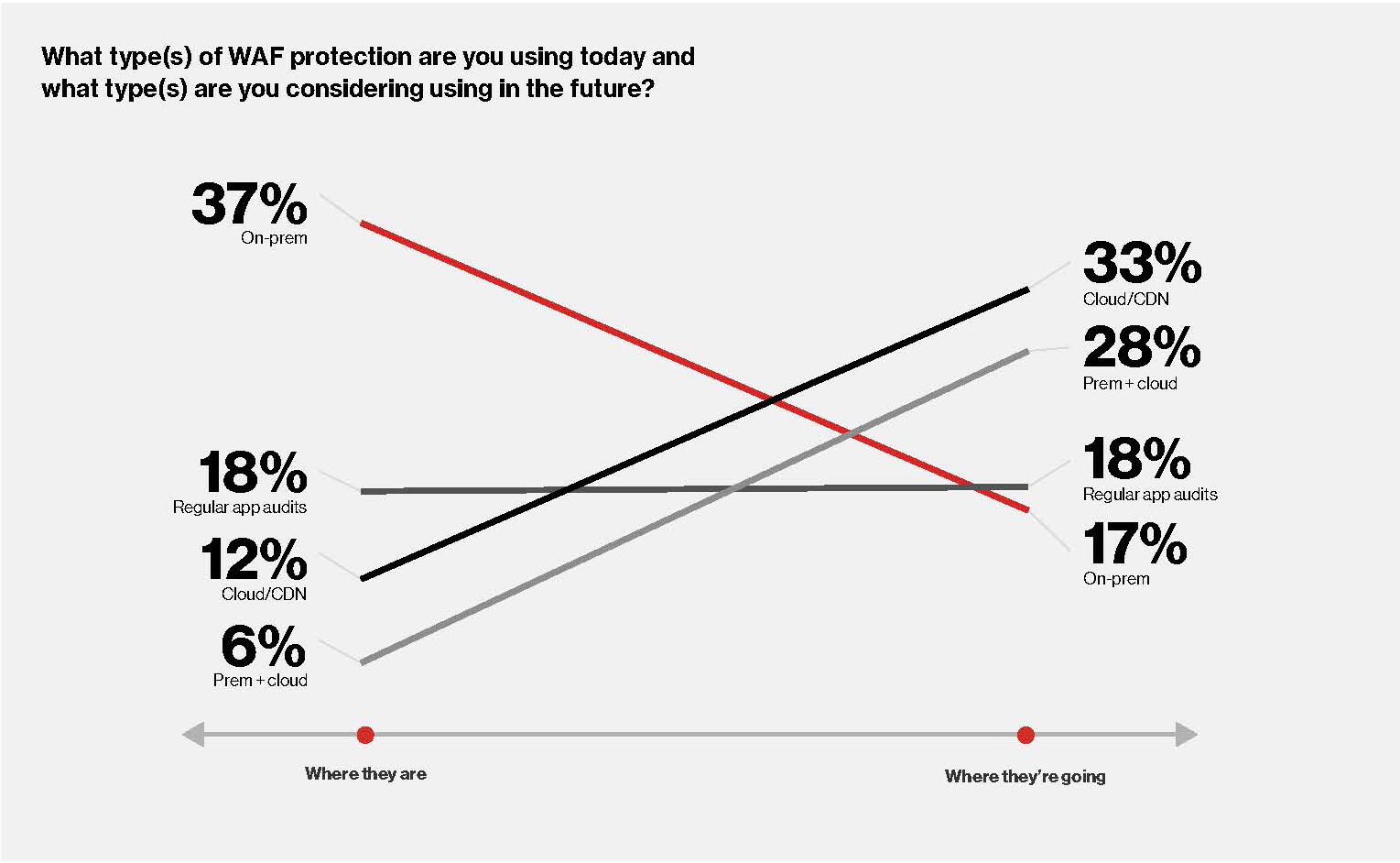
However, user dissatisfaction and high failure rates reflect that WAFs are difficult to set up and require constant monitoring. They are also costly to buy and to maintain. Verizon Media’s answer to these issues is to use a cloud-based WAF solution which among other benefits is as-a-Service so there’s less on-prem maintenance.
Bot Management
Bot management is the third major weapon in the anti-cybercrime armory. Bots are useful for many things – they help keep support costs low by assisting users to self-diagnose problems. They also help Google, Bing, and Yahoo index the web. However, they’ve also become an indispensable tool for criminals. Attackers use bots to orchestrate DDoS attacks and handle the massive number of login attempts required for credential stuffing attacks.
Bot management solutions integrated into a cloud or CDN service provider can come to the rescue, Verizon Media says. The cloud or CDN provider handles all aspects of the bot management solution for the service provider.
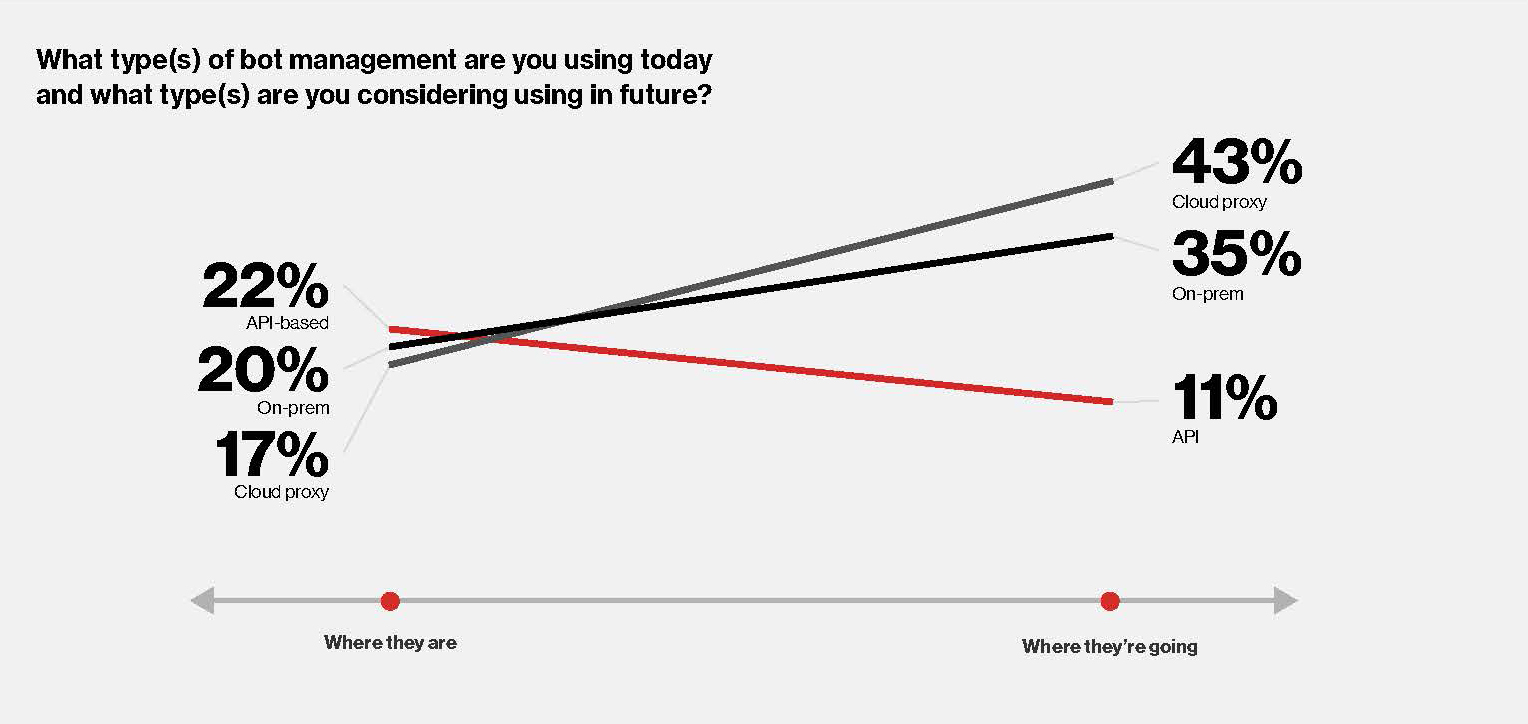
As content providers, streaming services and broadcasters migrate more activity to the cloud, many of these cloud-based protections will automatically follow.
The overriding strategy must be to use all these defences and more to combat attacks. Hopefully, you have already rolled out security solutions to handle the most common types of cyberattacks but if not this may provide food for thought.